What is Computer Networks?

A computer network is a system that connects two or more computing devices, allowing them to share resources and exchange information. These devices, often referred to as nodes, can include personal computers, servers, printers, and various other hardware components. The connections between these nodes can be established using wired or wireless communication methods.
Key Components
-Nodes: These are the individual devices in a network, such as computers, servers, and networking hardware (e.g., routers and switches) that facilitate data transmission.
-Links: The physical or wireless connections that enable communication between nodes.
-Protocols: A set of rules governing data transmission over the network. Common protocols include TCP/IP (Transmission Control Protocol/Internet Protocol), which is fundamental to internet connectivity.
Types of Networks
Computer networks can be classified based on various criteria, including their size, geographical coverage, and purpose. Here are the main types:

-Personal Area Network (PAN): Connects devices within a very short range, typically around one person. Technologies like Bluetooth are commonly used here.
-Local Area Network (LAN): Covers a small geographical area, such as a home or office. It allows multiple devices to communicate and share resources.
-Metropolitan Area Network (MAN): Spans a city or large campus, connecting multiple LANs.
-Wide Area Network (WAN): Covers a broad area, potentially connecting devices across countries or continents.
-Storage Area Network (SAN): A specialized network designed to provide access to consolidated block-level data storage.
Network Topology and Its Types
Network topology refers to the arrangement of different elements (links, nodes, etc.) in a computer network. The main types include:
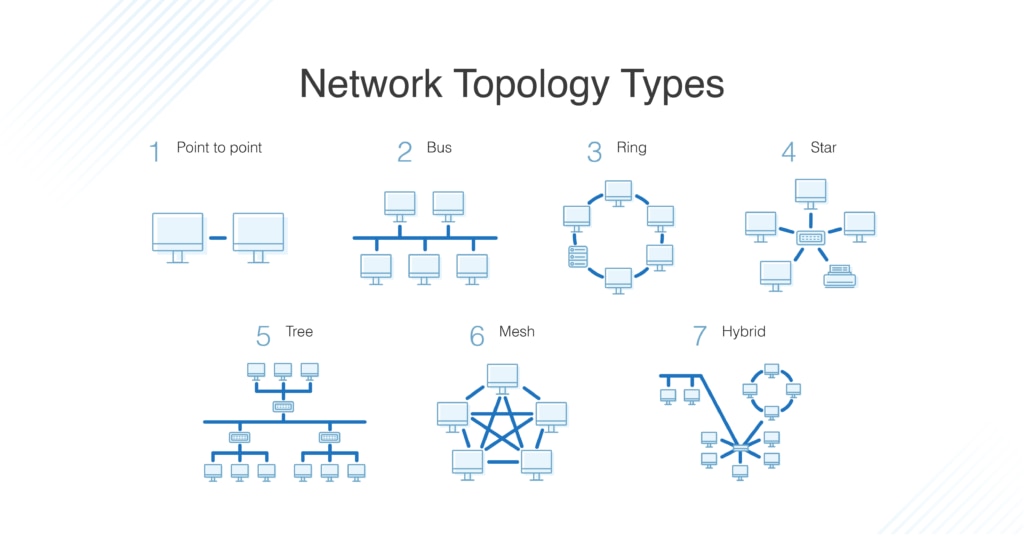
Bus Topology: All devices share a single communication line.
Star Topology: All nodes connect to a central hub; if one connection fails, others remain unaffected.
Ring Topology: Each device connects to two others, forming a circular pathway for data.
Mesh Topology: Devices are interconnected; can be full mesh (every device connects to every other) or partial mesh (some devices connect).
Tree Topology: A hybrid of star and bus topologies; it features a central root node with branches.
OSI and TCP/IP Models
OSI Model

The OSI (Open Systems Interconnection) model consists of seven layers:
Physical Layer: Deals with the physical connection between devices.
Data Link Layer: Provides node-to-node data transfer and error correction.
Network Layer: Handles routing and forwarding of data packets.
Transport Layer: Ensures complete data transfer and error recovery.
Session Layer: Manages sessions between applications.
Presentation Layer: Translates data formats between the application layer and the network.
Application Layer: Interfaces with end-user applications.
TCP/IP Model
The TCP/IP model has four layers:

Link Layer: Corresponds to the OSI's Physical and Data Link layers.
Internet Layer: Similar to the OSI's Network layer; it handles packet routing through IP addresses.
Transport Layer: Equivalent to the OSI's Transport layer; it includes protocols like TCP and UDP for data transfer.
Application Layer: Combines the OSI's Application, Presentation, and Session layers.
Synchronous vs Asynchronous Switching
Synchronous Switching: Data is transmitted at regular intervals; timing is crucial for synchronization between sender and receiver.
Asynchronous Switching: Data can be sent at any time without synchronization; it allows for more flexible communication.
Routing and Error Correction
Types of Error-Correcting Codes
Error-correcting codes help detect and correct errors in data transmission. Common types include:
Hamming Code: Detects up to two-bit errors and corrects one-bit errors.
Reed-Solomon Code: Used in CDs and DVDs; it can correct multiple errors in blocks of data.
Bose–Chaudhuri–Hocquenghem (BCH) Codes: Generalized error-correcting codes capable of correcting multiple random errors.
Difference Between Error Correction and Error Detection
Error Detection identifies that an error has occurred but does not correct it.
Error Correction not only identifies but also corrects the errors in the transmitted data.
Shortest Path Algorithm
The shortest path algorithm finds the most efficient route from one node to another in a network. Dijkstra's algorithm is one of the most commonly used methods for this purpose.
Dijkstra’s algorithm is a well-known shortest path algorithm that operates on a graph representation of the road network, where intersections are nodes and roads are edges. This algorithm systematically explores the graph by:
Initialization: Starting from the source node (the user's current location), it assigns a tentative distance value to every node, initially set to infinity, except for the source node which is set to zero.
Exploration: It repeatedly selects the node with the smallest tentative distance, explores its neighbors, and updates their distances based on the current node's distance plus the edge weight (representing distance or time).
Completion: The process continues until all nodes have been visited or the destination node's shortest path has been determined.
Dijkstra’s algorithm guarantees finding the shortest path but does not account for dynamic factors like traffic congestion or road conditions
Distance Vector Routing
Distance vector routing protocols determine the best path for data packets based on distance metrics. Each router shares its knowledge about the entire network with its immediate neighbors.
Connection vs Connectionless Services
-Connection Services establish a dedicated communication path before transmitting data (e.g., TCP).
-Connectionless Services send data without establishing a dedicated path (e.g., UDP).
What is the Network Layer?
-768.png)
The network layer is responsible for routing packets across different networks. It manages logical addressing (IP addresses) and determines how packets are forwarded.
Routing Algorithms
Routing algorithms determine how packets travel through a network. Common types include:
Routing algorithms can be classified into various types, including:
Adaptive Algorithms: These algorithms adjust their routing decisions based on changes in network topology or traffic conditions. They are often used in dynamic environments where real-time data is available.
Non-Adaptive Algorithms: These do not change once set and are typically used in simpler networks.
Hybrid Algorithms: A combination of both adaptive and non-adaptive methods, allowing for flexibility in routing decisions.
In the context of Google Maps, the focus is primarily on adaptive algorithms due to the need for real-time updates and traffic considerations
Internet Control Protocols
Internet control protocols are crucial for the functioning of networks, enabling communication and management of data transmission. Here’s a detailed explanation of key Internet control protocols: ARP, ICMP, IGMP, and RARP.
ARP (Address Resolution Protocol)
Functionality: ARP is used to map an IP address to a physical MAC (Media Access Control) address within a local area network (LAN). This mapping is essential because while devices communicate over a network using IP addresses, the actual data transmission occurs at the link layer using MAC addresses.
How it Works:
ARP Request: When a device wants to communicate with another device on the same network and knows its IP address but not its MAC address, it broadcasts an ARP request packet. This packet asks, "Who has IP address X.X.X.X? Please send me your MAC address."
ARP Reply: The device with the matching IP address responds with an ARP reply that includes its MAC address.
Caching: The requesting device caches this information for future communications to minimize network traffic.
Use Case: For example, when a computer wants to send data to a printer on the same network, it uses ARP to find out the printer's MAC address associated with its IP address.
ICMP (Internet Control Message Protocol)
Functionality: ICMP is primarily used for error reporting and operational information exchange in IP networks. It helps manage and control network operations by sending messages about issues in data transmission.
Key Messages:
Echo Request/Reply: Used by tools like ping to test connectivity between devices by sending an echo request and expecting an echo reply.
Destination Unreachable: Sent when a packet cannot reach its destination due to various reasons (e.g., host down or network unreachable).
Time Exceeded: Indicates that a packet's Time to Live (TTL) has expired, often used in diagnostic tools like traceroute.
How it Works:
ICMP messages are encapsulated within IP packets. When an error occurs, routers or hosts send ICMP messages back to the source of the original packet, allowing for diagnosis and troubleshooting of network issues. For instance, if a router cannot forward a packet due to lack of a route, it sends back an ICMP Destination Unreachable message.
IGMP (Internet Group Management Protocol)
Functionality: IGMP is used for managing multicast group memberships on IP networks. It allows hosts and adjacent routers to communicate about multicast group memberships.
How it Works:
Joining a Group: When a host wants to receive multicast traffic (e.g., streaming video), it sends an IGMP membership report to join a specific multicast group.
Leaving a Group: When the host no longer wishes to receive that traffic, it sends an IGMP leave message.
Router Interaction: Routers use IGMP to learn which hosts are interested in receiving multicast traffic so they can optimize data delivery.
Use Case: IGMP is commonly used in applications such as IPTV or online gaming where multiple users receive the same data stream simultaneously.
RARP (Reverse Address Resolution Protocol)
Functionality: RARP is used by a device to discover its own IP address from its MAC address. This protocol is particularly useful for diskless workstations that do not have permanent storage.
How it Works:
RARP Request: A device sends out a RARP request containing its MAC address.
RARP Reply: A RARP server on the network responds with the corresponding IP address associated with that MAC address.
Configuration: The device then configures itself with the received IP address for further communication on the network.
Use Case: RARP was commonly used in early networking setups where devices booted from a network server and needed to obtain their IP addresses dynamically.
What is the Transport Layer?
The transport layer ensures reliable data transfer between devices. Key elements include:
Protocols:
TCP (Transmission Control Protocol): Provides reliable, ordered delivery of data packets.
UDP (User Datagram Protocol): Offers faster transmission without guaranteed delivery.
UDP vs TCP
UDP:
Connectionless protocol
Faster but less reliable
Suitable for applications like streaming where speed is prioritized over reliability.
TCP:
Connection-oriented protocol
Ensures reliable delivery
Suitable for applications like web browsing where accuracy is crucial.
Application Layer Protocols
Five common protocols at the application layer include:
HTTP (Hypertext Transfer Protocol)
FTP (File Transfer Protocol)
SMTP (Simple Mail Transfer Protocol)
DNS (Domain Name System)
Telnet
Difference Between HTTP and HTTPS
The difference between HTTP (Hypertext Transfer Protocol) and HTTPS (HTTP Secure) is significant, particularly concerning security and data integrity.
HTTP (Hypertext Transfer Protocol)
Security: HTTP is an unsecured protocol, meaning that data transmitted between the client and server is sent in plaintext. This makes it vulnerable to interception and eavesdropping by malicious actors.
Port Number: HTTP operates over port 80 by default. This is the standard port for web traffic that does not require encryption.
Data Transmission: Data sent via HTTP can be easily read by anyone who intercepts the communication. This includes sensitive information such as login credentials, personal data, and payment information, which can be exploited if transmitted over HTTP.
Performance: Generally, HTTP may offer slightly faster performance compared to HTTPS because it does not involve the overhead of encryption and decryption processes. However, this speed comes at the cost of security.
Stateless Protocol: HTTP is a stateless protocol, meaning that each request from a client to a server is treated independently without retaining any session information from previous requests. This can limit functionality in applications that require session management.
SEO Impact: Websites using HTTP may be penalized in search engine rankings compared to those using HTTPS, as search engines like Google prioritize secure sites in their algorithms.
HTTPS (HTTP Secure)
Security: HTTPS provides a secure communication channel by encrypting data transmitted between the client and server using SSL/TLS (Secure Sockets Layer/Transport Layer Security). This encryption protects against dropping and man-in-the-middle attacks.
Port Number: HTTPS operates over port 443 by default, which is designated for secure web traffic. This distinction helps browsers identify secure connections.
Data Transmission: Data sent via HTTPS is encrypted, making it unreadable to anyone who intercepts it. This is crucial for protecting sensitive information such as passwords, credit card numbers, and personal details during transmission.
Performance: While HTTPS may introduce some latency due to the encryption process, advancements in technology (such as HTTP) have significantly reduced this impact, making HTTPS performance comparable to or even faster than HTTP in many cases.
Session Management: HTTPS supports secure session management through mechanisms like cookies with the Secure attribute, which ensures that cookies are only sent over secure connections. This enhances user experience while maintaining security.
SEO Benefits: Websites utilizing HTTPS are favored by search engines, which can improve their visibility and ranking in search results. This has become increasingly important as users seek secure browsing experiences.
Difference Between FTP and SMTP
FTP (File Transfer Protocol)
Purpose and Functionality
FTP is specifically designed for transferring files between computers over a network, typically the internet. It provides a standard method for:
Uploading files to a remote server
Downloading files from a remote server
Managing files and directories on remote systems
Key Characteristics
Uses a client-server model
Typically operates on two ports:
Port 21 for control connection
Port 20 for data transfer
Supports two modes of authentication:
Anonymous login (public access)
Specific username and password
Allows bidirectional file transfer
Supports large file transfers
Can maintain directory structures during transfers
Use Cases
Web hosting file management
Sharing large files between organizations
Backing up and synchronizing files
Software distribution
SMTP (Simple Mail Transfer Protocol)
Purpose and Functionality
SMTP is specifically designed for sending and routing email messages between email servers across networks. Its primary role is to:
Transmit email from a sender's email client to the recipient's email server
Route emails between different email servers
Ensure reliable email delivery
Key Characteristics
Uses a client-server model for email transmission
Typically operates on port 25 (standard), port 587 (secure)
Follows a strict message format with headers and body
Works in conjunction with other protocols like POP3 and IMAP
Supports email queuing and retry mechanisms
Includes basic error reporting and handling
Use Cases
Sending emails from personal or business email accounts
Routing emails between different email servers
Enabling communication across different email platforms and domains
Comparison and Key Differences
| Aspect | FTP | SMTP |
| Primary Purpose | File transfer | Email transmission |
| Data Type | Any type of file | Text-based email messages |
| Network Layer | Focuses on file movement | Focuses on message routing |
| Authentication | Username/password or anonymous | Typically requires email credentials |
| Security | Basic authentication | Supports encryption (SMTPS) |
| Typical Ports | 20 (data), 21 (control) | 25 (standard), 587 (secure) |
Security Considerations
Both protocols have evolved to support more secure versions:
FTPS (FTP Secure) with SSL/TLS encryption
SMTPS (SMTP Secure) with SSL/TLS encryption
Modern implementations emphasize secure, encrypted connections
Modern Alternatives
SFTP (SSH File Transfer Protocol) for more secure file transfers
HTTPS for secure web-based file uploads
Secure email protocols like SMTP with STARTTLS for enhanced email security
While FTP and SMTP might seem similar in that they both transfer data across networks, they serve fundamentally different purposes. FTP is about moving files, while SMTP is about routing email messages.
